Secure WordPress is an everyday work. I’m not talking about WordPress core but the whole Website.
There is things you can do once, but sometimes check if this rules are still efficients.
The waves of attacks on WordPress Websites came sometimes, and it’s very hard or even impossible to predict.
4 easy rules to do once
Change the Database Prefix
You may already know, you shouldn’t use neither wp_ neither wordpress_ as a database prefix. But do you know why?
The explanation is relatively simple. When a SQL Injection vulnerability is exploited, the attacker needs to target your tables, for example he needs wp_users to read your informations. But what if the prefix wasn’t wp_ then he’ll got errors, only.
The security tip will be to use a long or random prefix. Remember that you won’t have to actually remember it, even if you’re a developper. Secure WordPress is also about securing your database!
Using SecuPress this fix is automatic:
Avoid the Directory Listing
In most of installations it’s possible to access to the content of your folders. It might seems harmless but it’s strongly advised to not let this happen.
Let’s imagine to have some documents only accessible with a paid account, or some others containing private informations or even some PHP file with dev tests which should not be available to your visitors, also reachable by search engines? This is not appropriate for security reasons.
You have so secure WordPress thinking about the environment settings. You only need a few lines of code in a particular config file (depending of your installation) and this listing will be forbidden.
You have to add a .htaccess file (if you’re running under Apache) including this code:
[pastacode lang=”php” manual=”%3CIfModule%20mod_autoindex.c%3E%0A%20%20%20%20Options%20-Indexes%0A%3C%2FIfModule%3E” message=”” highlight=”” provider=”manual”/]
Using SecuPress this fix is done with only one click :
Choose a Strong Password
We, humans, like simplicity, our brain doesn’t like complex things, on the contrary.
When we talk about passwords, the effort to make a complex choice is not easy to do.
But when we talk to secure WordPress, the users are also personaly in charge of this security level.
I recommand you to read this post about strong passwords, then you’ll quickly understand why your users should follow this example.
SecuPress can force your users to set a strong password to secure WordPress:
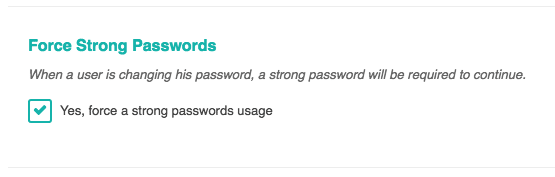
Force a strong password for your users with SecuPress
Deactivate the Plugins and Themes Tile Editor
File edition is usually done on your computer using a code editor. For CSS files or PHP files, you’ll then use a FTP software to upload these files on our Website.
But WordPress allows everyone to directly edit files from the administration screen. Talking about security, it’s very and too much dangerous. Let the possibility, even for an administrator, to edit a .php file if a huge danger and stop you to correctly secure WordPress.
This is not because someone is an administrator that he has the right to modify your files, this is absolutly two differents things!
This line of code deactivate the native file editor from WordPress, place this is your wp-config.php file:
[pastacode lang=”php” manual=”define(‘DISALLOW_FILE_EDIT’%2C%20true)%3B” message=”” highlight=”” provider=”manual”/]
SecuPress checks and fixes for you this setting which depends on your wp-config.php
With these 4 rules fixed, you’ll have succeed to secure WordPress a little more, do you know some others simple rules that requires only one step forever to share with us?










